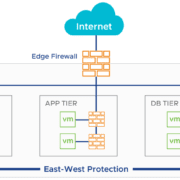
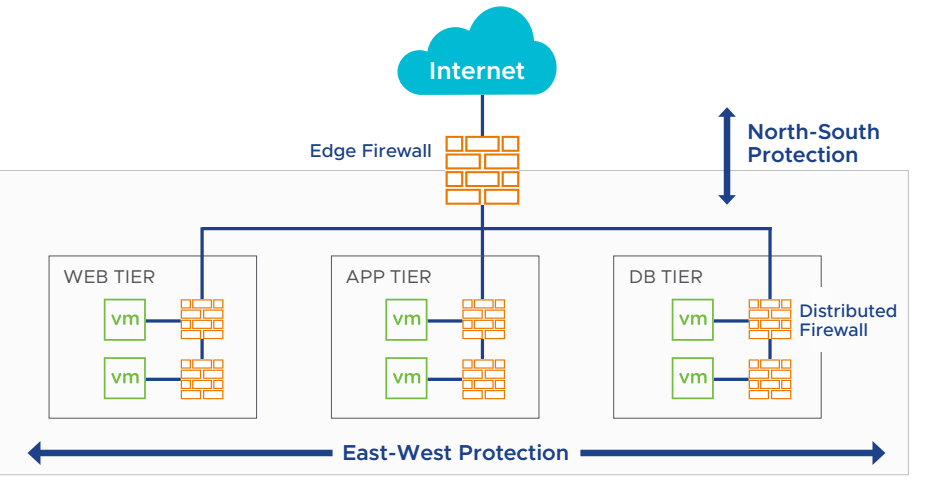
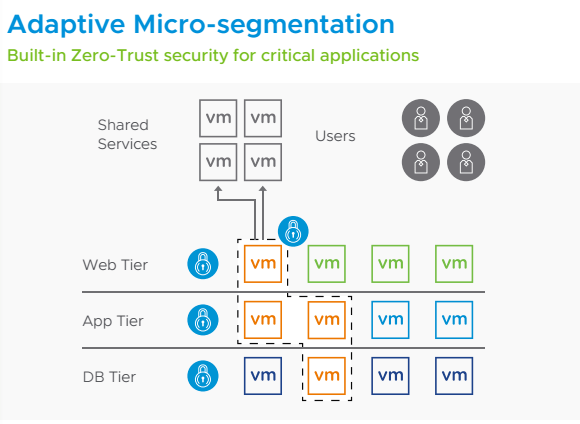
Globally, 30,000 websites are hacked daily. Every 39 seconds, there is a new attack somewhere on the web.
Trust is paramount to any business transacting online.
GDMS is supporting businesses in building trust and security across Asia. We offer a wide range of security certificates such as SSL certificates (wildcard, OV, DV…), Email Signing Certificates, and Web Security Solutions.
What SSL Certificates matter
Now that browsers display “Not Secure” warnings for webpages served over HTTP, making the decision to protect your entire website with SSL/TLS certificates is a no-brainer. What’s not so obvious is which type of certificate makes the most sense.
Without guidance, choosing the right SSL certificate can be a bit overwhelming. But, it’s way too important to be left to chance. Your online reputation and success depend on making an informed decision. Online buyers get savvier by the minute, and website security solution says a lot more about you than you think. Here are the key factors to consider when deciding which SSL certificate is right for you.
How many domains and sub-domains do you need to protect?
Single SSL certificates secure one domain name or URL. When you have multiple domains and subdomains to protect, things can get a little pricey and tough to manage. That’s where Wildcard and Multi-domain certificates come in. They save you money and simplify management.
How important is identity validation?
Trust is today’s most valuable currency online—no matter what type of website you have. All SSL certificates include encryption to protect data in transit, including usernames, passwords, and credit card information. But, you need to decide what level of identity authentication, also known as validation, is enough for your visitors to feel comfortable without a doubt that you’re a legitimate organization and not some phishing site. The more premium the SSL certificate, the more in-depth the validation, the more visible the visual trust indicators, and the more confident your visitors.
What are your goals?
If your online reputation is a key factor in your success and your goal is to maximize conversions, trust is essential. Studies show 69% of online shoppers specifically look for websites that display trust symbols. display instantly recognizable visual indicators, plus are proven to increase sales.
How much risk can you afford?
SSL certificates typically come with a warranty so, in the event of a hack or data breach that results from a flaw in the certificate, you’re covered. Warranty levels vary, with some lower-end certificates—such as DV and a few OVs—covering up to $10,000 in damages and some higher-end products offering up to $1,750,000 in coverage.
General rules of thumb
If you’re running a blog or personal non-e-commerce website, a Domain Validation (DV) SSL certificate is probably sufficient. They’re fast, have no frills, and provide basic encryption with domain-only validation.
If proving your organization is legit matters, but EV is outside your budget, an Organization Validation (OV) SSL certificate might be a good fit. It provides a bit more authentication and comes with a clickable dynamic site seal, so visitors can feel more confident it’s really you on the other end. For eCommerce sites, OV should be the absolute minimum.
If you’re a national or global brand, want to maximize confidence and conversions, and clearly show customers their security is one of your top priorities, an Extended Validation (EV) SSL certificate is the way to go. The authentication process is the most extensive, so it takes a little longer, but the payoff is it comes with the green address bar—the most universally trusted symbol across the web. It’s impossible to fake so it’s the ultimate trust builder. One Tec-ED study even showed EV is proven to increase conversions.
Still not sure? We’re here to help.